03 November, 2007

 No Starch Press
No Starch Press has posted
Chapter 10: Deploying fwsnort
for free
download on their
site. This chapter concentrates on the application of
fwsnort
to iptables rulesets, as mentioned in the chapter introduction:
 With the theoretical
discussion in Chapter 9 on the emulation of Snort rule options within iptables
behind us, we'll talk in this chapter about how to get fwsnort to actually do
something! Namely, we'll discuss the administration of fwsnort and illustrate
how it can be used to instruct iptables to detect attacks that are associated
with the Snort signature ruleset.
With the theoretical
discussion in Chapter 9 on the emulation of Snort rule options within iptables
behind us, we'll talk in this chapter about how to get fwsnort to actually do
something! Namely, we'll discuss the administration of fwsnort and illustrate
how it can be used to instruct iptables to detect attacks that are associated
with the Snort signature ruleset.
When fwsnort is executed from the command line with no restrictive
arguments to limit the scope of the translation process, the default
output displays the success and failure rates for translating Snort
signatures as seen below. Not all Snort signatures can be re-cast
into an iptables rule because of complexities (such as PCRE's) that
cannot (yet) be handled within iptables, but as you can see fwsnort
achieves a 60% translation rate for the Snort-2.3.3 ruleset - this
is more than sufficient to catch a lot of malicious traffic.
[iptablesfw]# fwsnort
Snort Rules File Success Fail Ipt_apply Total
[+] attack-responses.rules 15 2 0 17
[+] backdoor.rules 62 7 1 69
[+] bad-traffic.rules 10 3 0 13
[+] bleeding-all.rules 1076 573 5 1649
[+] exploit.rules 31 43 0 74
[+] web-cgi.rules 286 62 0 348
[+] web-client.rules 7 10 0 17
[+] web-coldfusion.rules 35 0 0 35
[+] web-frontpage.rules 34 1 0 35
[+] web-iis.rules 103 11 0 114
[+] web-misc.rules 265 61 0 326
[+] web-php.rules 78 48 0 126
[+] x11.rules 2 0 0 2
2725 1761 91 4486
[+] Generated iptables rules for 2725 out of 4486 signatures: 60.74%
[+] Found 91 applicable snort rules to your current iptables policy.
[+] Logfile: /var/log/fwsnort.log
[+] Iptables script: /etc/fwsnort/fwsnort.sh
The chapter goes on to give several specific attack examples, and
how fwsnort can be used to detect them. Here is an example
Bleeding Edge
Snort rule for detecting the
Dumador Trojan
(which affects Windows systems and contains both a keylogger and a backdoor):
alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:"BLEEDING-EDGE \
TROJAN Dumador Reporting User Activity"; flow:established,to_server; \
uricontent:".php?p="; nocase; uricontent:"?machineid="; nocase; \
uricontent:"&connection="; nocase; uricontent:"&iplan="; nocase; \
classtype:trojan-activity; reference:url,www.norman.com/Virus/ \
Virus_descriptions/24279/; sid:2002763; rev:2;)
By using the fwsnort
--snort-sid command line argument, fwsnort will
build an iptables command that detects a specific Snort rule ID, so we use
this to restrict fwsnort's translation process to just the Dumador signature:
[iptablesfw]# fwsnort --snort-sid 2002763
[+] Parsing Snort rules files...
[+] Found sid: 2002763 in bleeding-all.rules
Successful translation.
The result is a rather complicated iptables command that uses the string
match extension multiple times to express the
uricontent fields in
the Snort rule. Also, the reference information and the Snort
msg
field are stored within the iptables rule with the
comment match.
Finally, the
FWSNORT_FORWARD_ESTAB iptables chain is used to only
perform the inspection over established TCP connections (the jump rule into
this chain uses the
state match):
$IPTABLES -A FWSNORT_FORWARD_ESTAB -s 192.168.10.0/24 -p tcp --dport 80 -m \
string --string ".php?p=" --algo bm -m string --string "?machineid=" --algo \
bm -m string --string "&connection=" --algo bm -m string --string "&iplan=" \
--algo bm -m comment --comment "sid:2002763; msg: BLEEDING-EDGE TROJAN \
Dumador Reporting User Activity; classtype: trojan-activity; reference: \
url,www.norman.com/Virus/Virus_descriptions/24279/; rev: 2; FWS:1.0;" -j LOG \
--log-ip-options --log-tcp-options --log-prefix "[1] SID2002763 ESTAB "
 The EnGarde Linux distribution, which focuses
on security, has announced
that they now bundle both fwknop and psad within
their latest release (3.0.18). Here is a quote from their press release:
The EnGarde Linux distribution, which focuses
on security, has announced
that they now bundle both fwknop and psad within
their latest release (3.0.18). Here is a quote from their press release:
 Guardian Digital is happy to announce the release of EnGarde Secure Community 3.0.18 (Version 3.0,
Release 18). This release includes many updated packages and bug fixes, some feature enhancements
to Guardian Digital WebTool and the SELinux policy, and a few new features.
Guardian Digital is happy to announce the release of EnGarde Secure Community 3.0.18 (Version 3.0,
Release 18). This release includes many updated packages and bug fixes, some feature enhancements
to Guardian Digital WebTool and the SELinux policy, and a few new features.
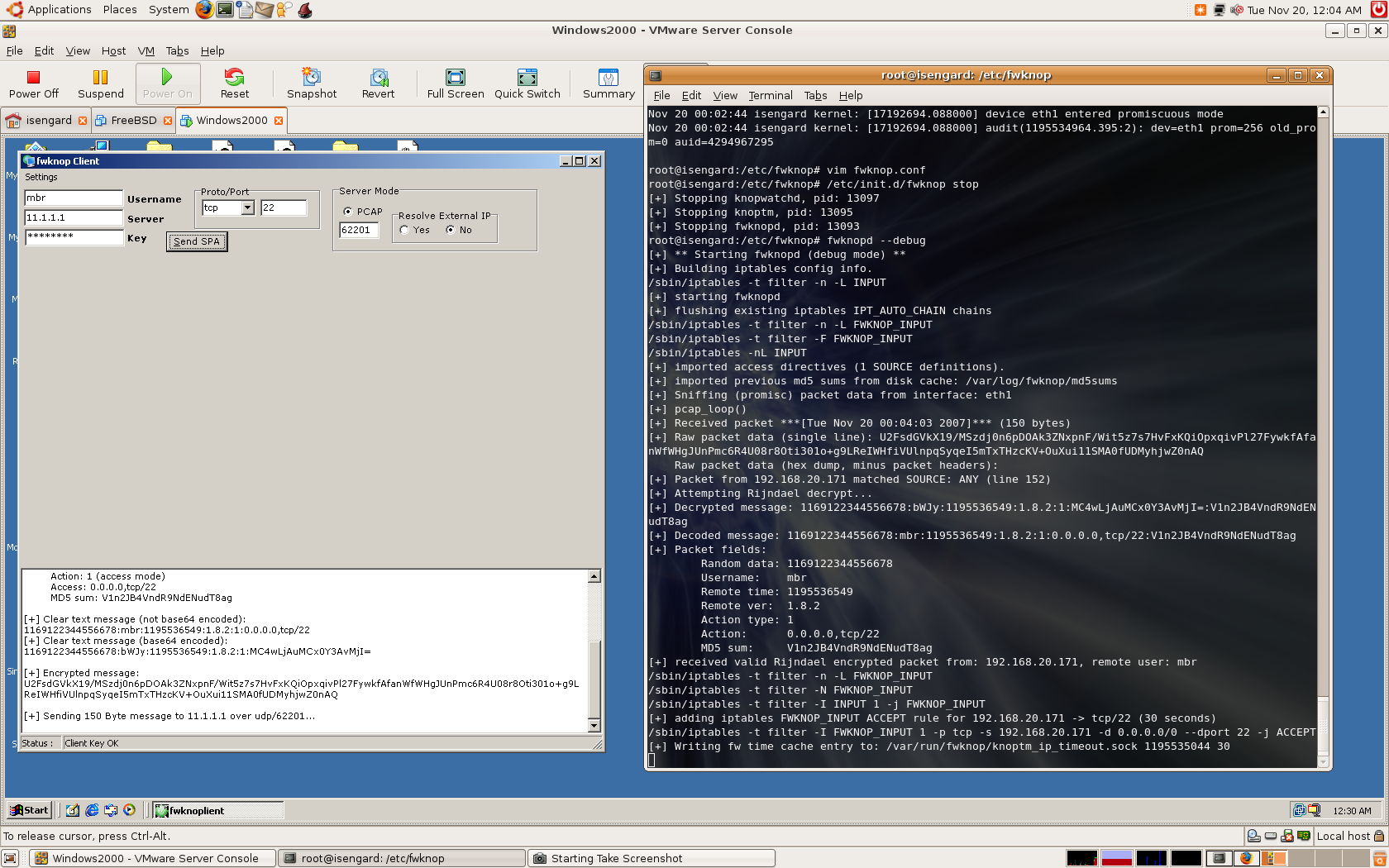
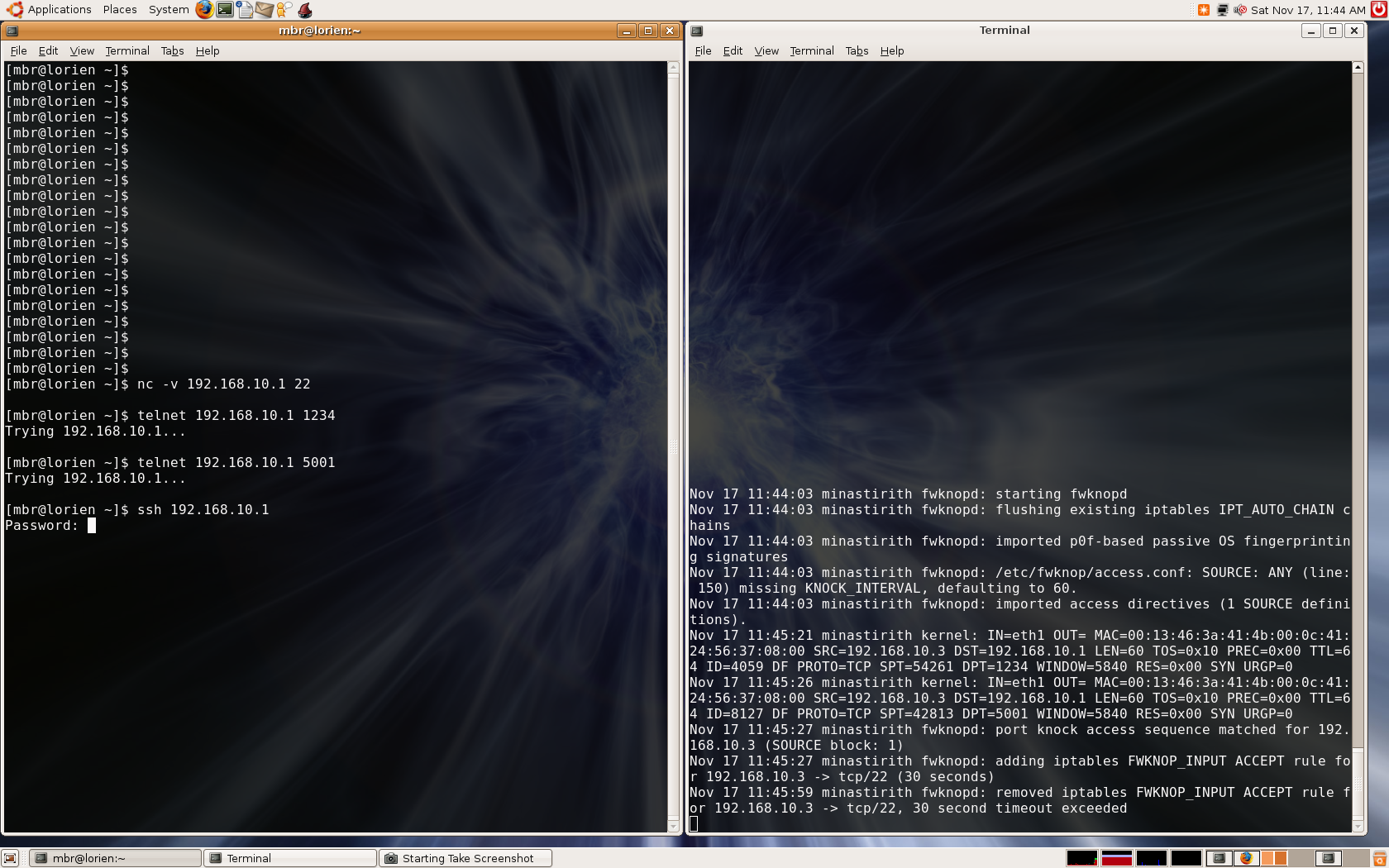
 This article will walk the reader through an EnGarde Secure Linux implementation of fwknop, from
the initial iptables rules setup to the deployment of fwknop on both the server and client side.
By the end of the article, the user will be able to explicitly shutdown all access to the EnGarde
Secure Linux SSH daemon to only those with fwknop credentials.
This article will walk the reader through an EnGarde Secure Linux implementation of fwknop, from
the initial iptables rules setup to the deployment of fwknop on both the server and client side.
By the end of the article, the user will be able to explicitly shutdown all access to the EnGarde
Secure Linux SSH daemon to only those with fwknop credentials.