17 November, 2007

The 1.8.3 release of
fwknop is ready for
download. This release reinstates
the legacy port knocking operation mode (for those that really want to use it instead
of
Single Packet Authorization). A few bugs have
also been fixed, particularly for the auto-resolution of external NAT addresses via
www.whatismyip.org (and a
backup resolution URL
exists now as well that you can hit with the
--URL option on the fwknop
client command line).
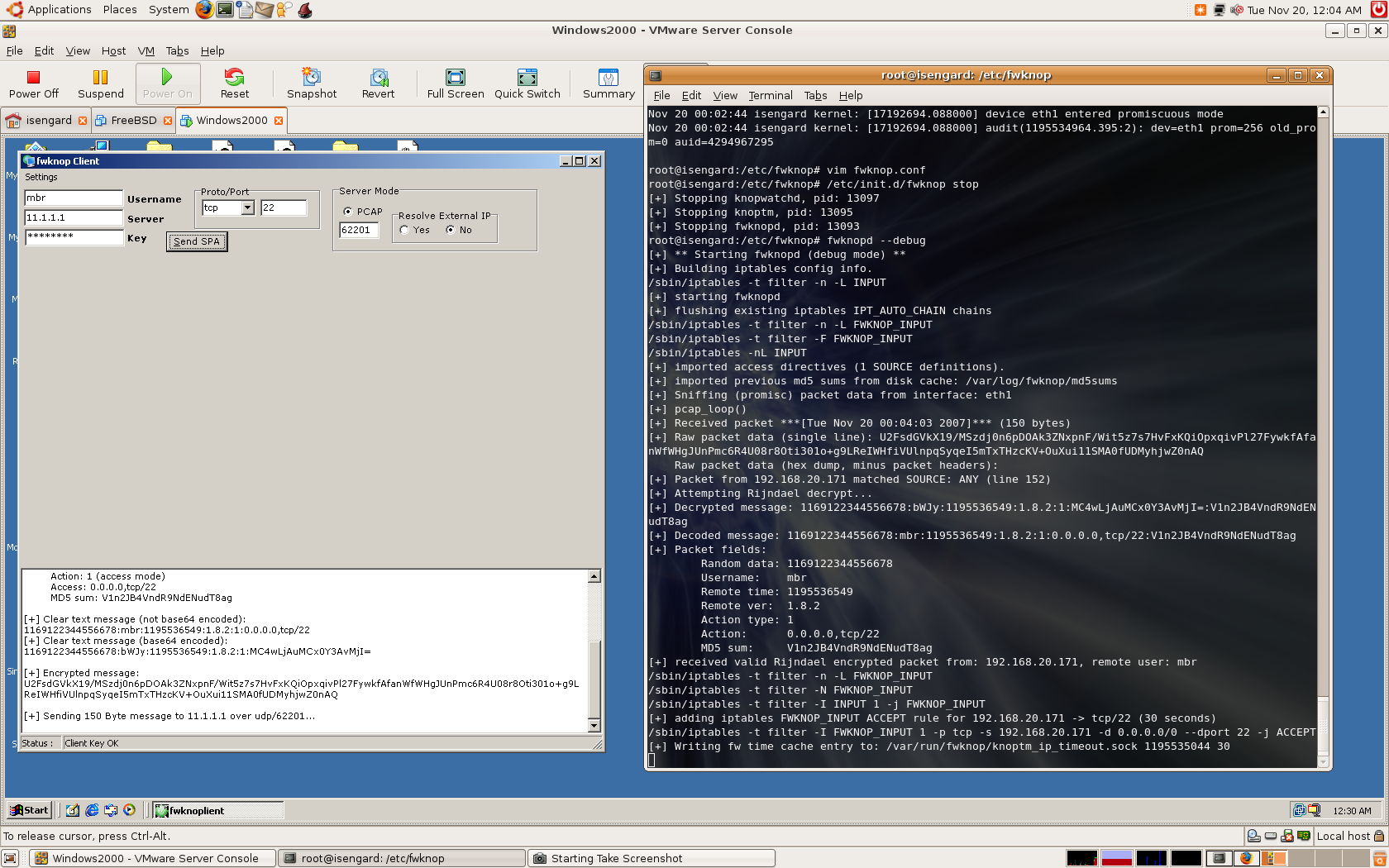
Below is an illustration of the old port knocking mode in
action. The fwknopd server running on 192.168.10.1 reconfigures the iptables policy
to allow an SSH connection from the client system 192.168.10.2 after receiving the
encrypted port knock sequence:
$ fwknop -A tcp/22 -a 192.168.10.2 -D 192.168.10.1 --Server-mode knock
[+] Starting fwknop client (encrypted port knocking mode)...
[+] Enter an encryption key. This key must match a key in the file
/etc/fwknop/access.conf on the remote system.
Encryption Key:
[+] Clear-text sequence (11 bytes): 192 168 10 2 0 22 6 28 109 98 114
[+] Cipher-text sequence (32 bytes): 83 97 108 116 101 100 95 95 110 133 220
202 45 184 129 230 175 166 62 162 104 46 183 22 193 82 17 126 174 38 76 222
[+] Sending port knocking sequence to knock server: 192.168.10.1
-> 192.168.10.1 tcp/61083 (packet: 0)
-> 192.168.10.1 tcp/61097 (packet: 1)
-> 192.168.10.1 tcp/61108 (packet: 2)
-> 192.168.10.1 tcp/61116 (packet: 3)
-> 192.168.10.1 tcp/61101 (packet: 4)
-> 192.168.10.1 tcp/61100 (packet: 5)
-> 192.168.10.1 tcp/61095 (packet: 6)
-> 192.168.10.1 tcp/61095 (packet: 7)
-> 192.168.10.1 tcp/61110 (packet: 8)
-> 192.168.10.1 tcp/61133 (packet: 9)
-> 192.168.10.1 tcp/61220 (packet: 10)
-> 192.168.10.1 tcp/61202 (packet: 11)
-> 192.168.10.1 tcp/61045 (packet: 12)
-> 192.168.10.1 tcp/61184 (packet: 13)
-> 192.168.10.1 tcp/61129 (packet: 14)
-> 192.168.10.1 tcp/61230 (packet: 15)
-> 192.168.10.1 tcp/61175 (packet: 16)
-> 192.168.10.1 tcp/61166 (packet: 17)
-> 192.168.10.1 tcp/61062 (packet: 18)
-> 192.168.10.1 tcp/61162 (packet: 19)
-> 192.168.10.1 tcp/61104 (packet: 20)
-> 192.168.10.1 tcp/61046 (packet: 21)
-> 192.168.10.1 tcp/61183 (packet: 22)
-> 192.168.10.1 tcp/61022 (packet: 23)
-> 192.168.10.1 tcp/61193 (packet: 24)
-> 192.168.10.1 tcp/61082 (packet: 25)
-> 192.168.10.1 tcp/61017 (packet: 26)
-> 192.168.10.1 tcp/61126 (packet: 27)
-> 192.168.10.1 tcp/61174 (packet: 28)
-> 192.168.10.1 tcp/61038 (packet: 29)
-> 192.168.10.1 tcp/61076 (packet: 30)
-> 192.168.10.1 tcp/61222 (packet: 31)
[+] Finished knock sequence.
$ ssh -l mbr 192.168.10.1
Password:
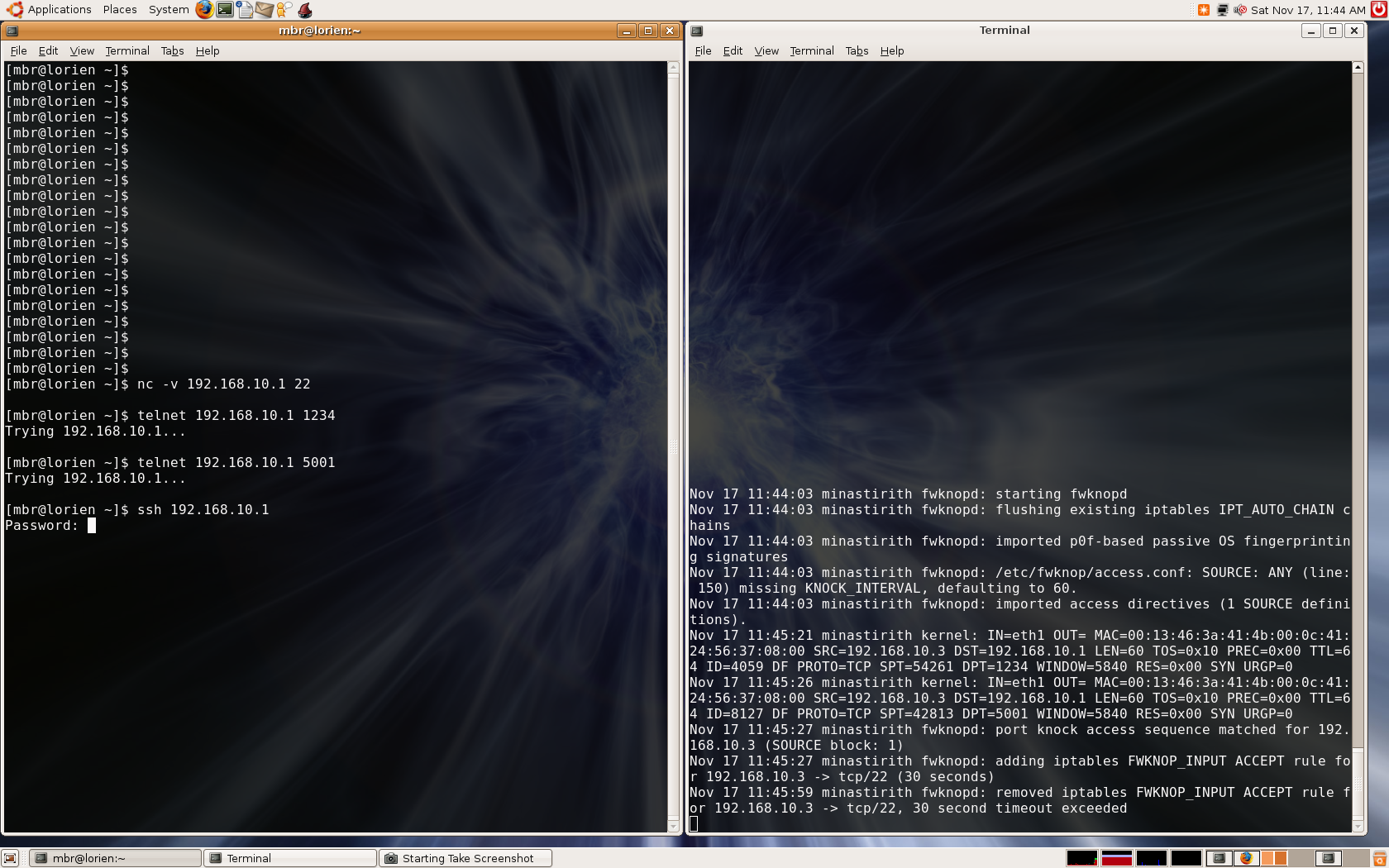
On the fwknopd server, the following messages are written to syslog that show an
iptables ACCEPT rule being added for the 192.168.10.2 client system for 30 seconds
and then removed. The SSH connection from the client remains open by using the
Netfilter connection tracking subsystem to allow packets in the ESTABLISHED state
through, but once the ACCEPT rule is removed no new SSH connections can be
established:
Nov 17 10:34:47 isengard fwknopd: successful knock decrypt for 192.168.10.2 (SOURCE block: 1)
Nov 17 10:34:47 isengard fwknopd: adding iptables FWKNOP_INPUT ACCEPT rule for 192.168.10.2 ->
tcp/22 (30 seconds)
Nov 17 10:35:19 isengard fwknopd: removed iptables FWKNOP_INPUT ACCEPT rule for 192.168.10.2 ->
tcp/22, 30 second timeout exceeded
Port knocking sequences do not necessarily have to be encrypted, and fwknop supports
shared sequences. This can be useful to allow systems where perl is not installed to
take advantage of some port knocking capabilities without requiring the fwknop client.
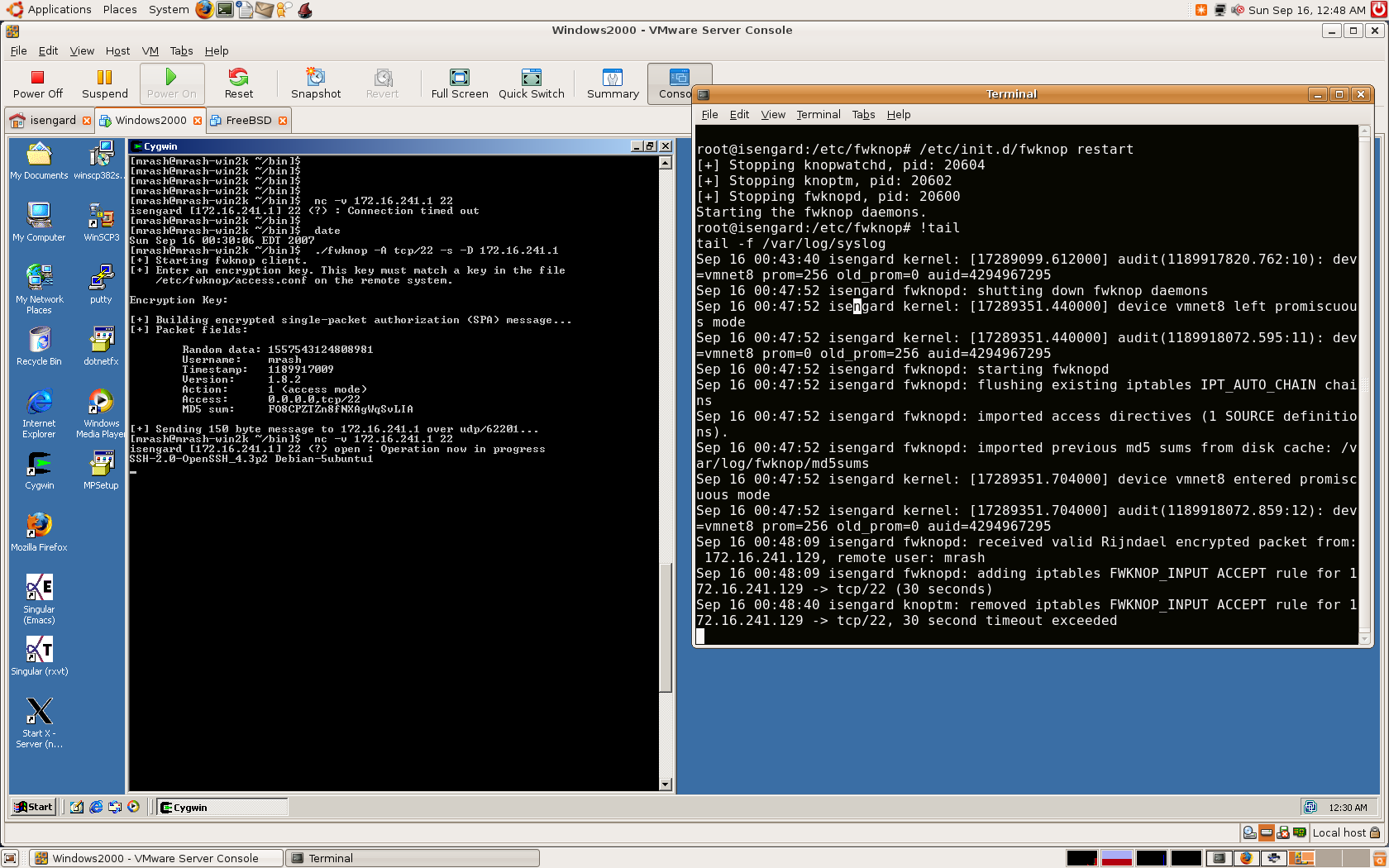
In the screenshot below, the fwknopd server (in the right hand
terminal) has been configured to accept a sequence that consists of the two TCP
ports 1234 followed 5001. The client (in the left hand terminal) just needs to use
any program such as netcat or telnet to hit these two ports, which generates iptables
log messages at the fwknopd server where the shared sequence is parsed and validated.
Once the correct sequence is seen, fwknopd opens port 22 for 30 seconds (this timeout
is configured in the /etc/fwknop/access.conf file):
For those interested in the changes in the fwknop-1.8.3 release, here is the complete
ChangeLog:
- Updated external IP resolution to point to http://www.whatismyip.org,
and added http://www.cipherdyne.org/cgi/clientip.cgi as a backup site
for fwknop IP resolution.
- Added storage of source IP along with SPA MD5 sum. This allows the user
to infer which networks are more hostile if an SPA packet is replayed.
- Added SPA packet hex dumps in 'fwknopd --debug' mode so that the
integration of third-party encryption algorithms is easier to
troubleshoot. Sean Greven contributed a patch for this.
- Reinstated the legacy port knocking mode. It appears that all encrypted
output from the updated Crypt::Rijndael module is at least 32 bytes
long, so port knocking sequences are now 32 bytes long as well (they
were previously 16 bytes long in old versions of fwknop).
- Bugfix to ensure the key length is at least 8 chars in --get-key mode.
- Minor update to remove init message on OS X install.
- Updated install.pl to set the LANG environmental variable to
"en_US.UTF-8". This should fix the problem where the output of ifconfig
was not interpreted correctly if the locale LANG setting is not English.
- Implemented verbose email alerting by setting the ALERTING_METHODS
variable to "verbose". This instructs fwknopd to generate a new email
message for each message that it normally logs vis syslog (this feature
is not the default, and must be manually enabled).
 The 2.1.1 release of psad is ready for
download. This release focuses
on support for some of the latest Linux distributions, such as Ubuntu 7.10 and
Fedora 8. There is also a new mode that allows psad to collect iptables logging
data directly from a file that is written to by syslog instead of via the previous
named pipe data collection mechanism. Here is the complete
ChangeLog:
The 2.1.1 release of psad is ready for
download. This release focuses
on support for some of the latest Linux distributions, such as Ubuntu 7.10 and
Fedora 8. There is also a new mode that allows psad to collect iptables logging
data directly from a file that is written to by syslog instead of via the previous
named pipe data collection mechanism. Here is the complete
ChangeLog: